Become a CloudFormation black belt
Today I joined an interesting webinar on Ben Bridts and Patrick Sard on cloudformation. A tool I have been using extensively. Mostly via the SAM abstraction for serverless applications.
What is Cloudformation
Define all the infrastructure that you want to have in the cloud in the form of Json or yaml.
Prefer yaml over json cause of readability and commenting.
Immutable template! -> Use the same template on different environments!
Anatomy of a template
Resources is the only required section in a cloudformation template.
You can use template functions in your cloudformation specification. Most used template Functions:
!Ref: reference another resource.!GetAtt: Get an attribute from another resource.!Sub: Do string interpolation.!Join: Concat strings / names.
Sometimes it is better to use
!Sub instead of !Join, for example:
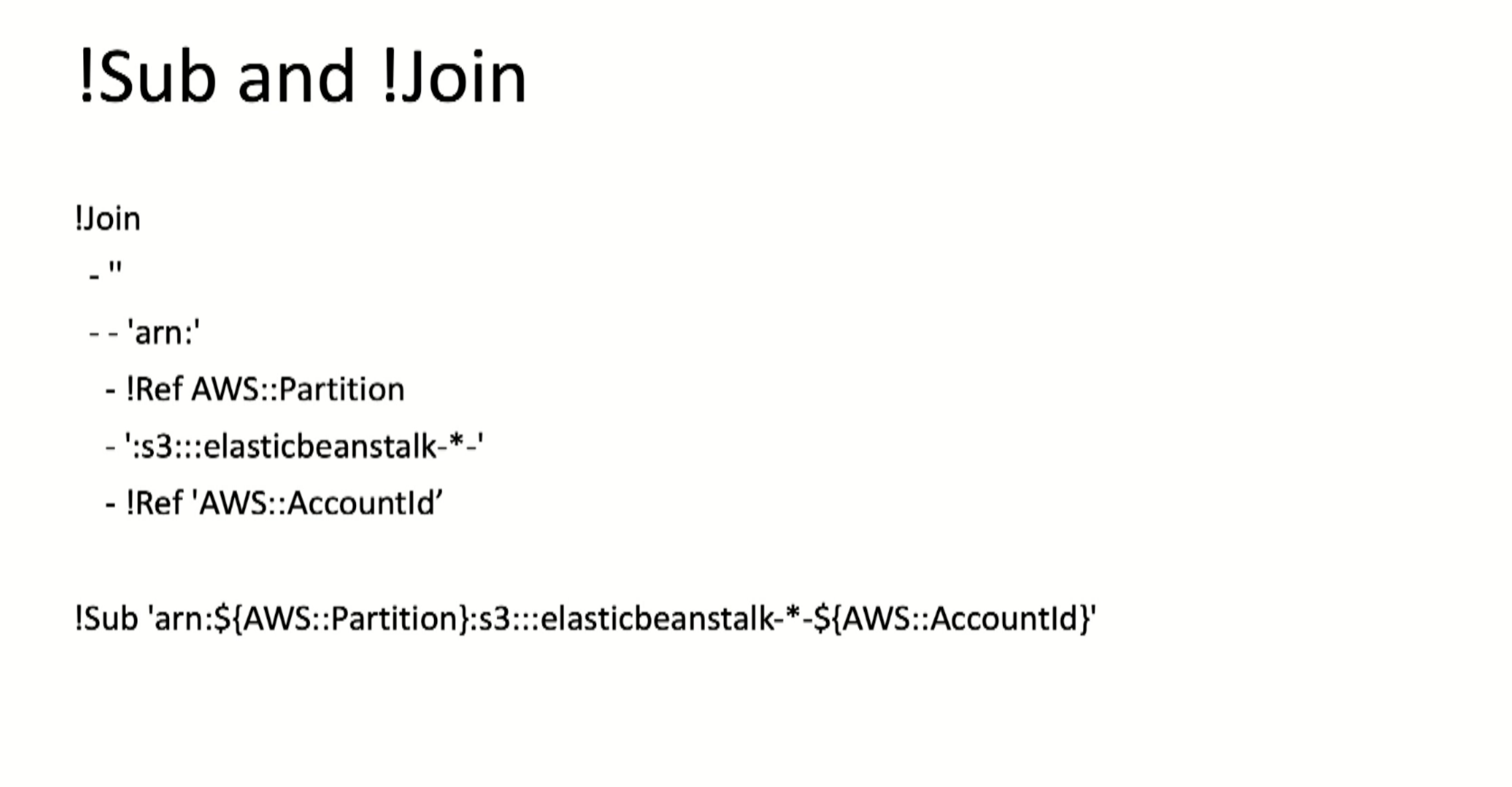
Tips:
- Let cloudformation name the resources.
- Use pseudo-parameters:
AWS::AccountIdandAWS::Region. These are parameters that are predefined by AWS CloudFormation. - Define rules: they give constraints to your template. You can for example specify which values are allowed
Tools
Tools to generate cloudformation
I imagine you don't like to write lot's of yaml.
Certainly not in the beginning when everything is new.
There are tools that can help you with that and will generate the `yaml for you when you drag-and-drop your services:
- Cloudformer
- Cloud Designer
- Stackery (for serverless apps)
Validate your template
- AWS command line: use the validate template command.
-
cfn-lint: first aid kit! Also for debunking cyclic dependencies.
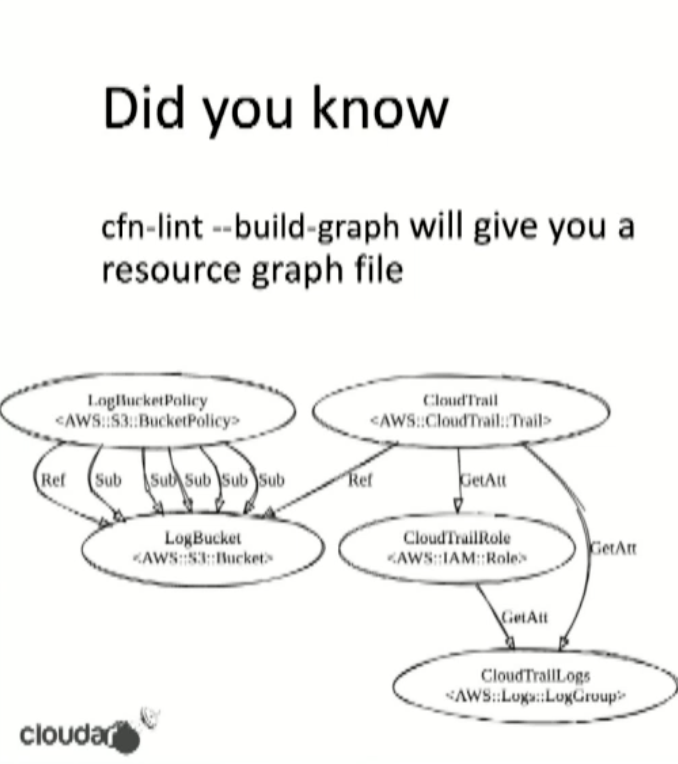
- cfn_nag: make your template more secure.
- taskcat: support multiple regions.
Pipelines
- Deploy to multiple accounts and environments.
- Deploy the same template to each account.
- Give cloudformation the right permissions to deploy the resources.
Give the right permissions to cloudformation and give the user a role to start the cloudformation deploy.
Or just usecodepipelineand givecodepipelinethe right permissions.
Features
- Features that are in the making are open for everyone. Check on Github.
- If you want to complain or do a shout out use the hashtag
#awswishliston Twitter.
Unsupported resources
Use Custom Resources or Resource Providers.
BTW, you can use terraform in cloudformation using resource providers.
Use resources from one stack in other stacks
There are two options:
- Export from one stack and import in another.
This will lock your resource.
You cannot rename or delete it by accident.
Export it first.


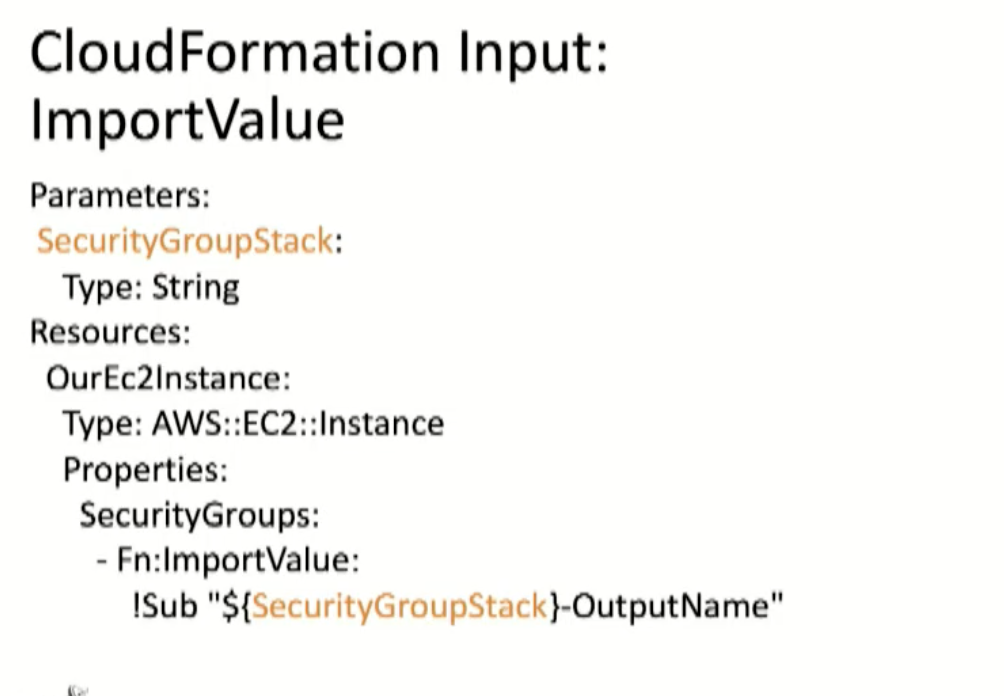
- Load into and out of ssm parameters.
Put it in the SSM parameter store:
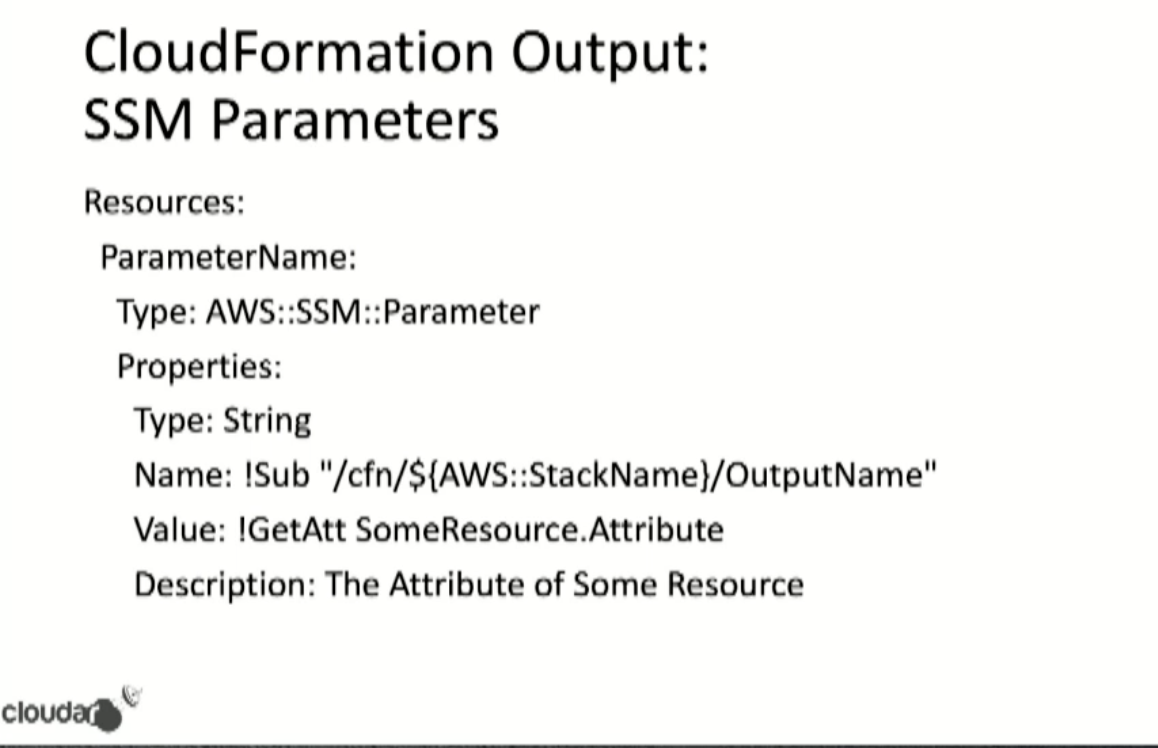

Credits
Based on a webinar by Ben Bridts and Patrick Sard from Cloudar an AWS. Featured image by Isis França on Unsplash.